What companies must do now – and what interim managers can contribute
The supply chain is the digital nervous system of modern companies. But the more connected, global, and complex it becomes, the more vulnerable it is to cyberattacks.
More and more attacks no longer target the company itself, but its service providers, suppliers, or software vendors. It’s a dangerous game of trust that can lead to severe economic damage. The challenge: even if your own systems are well protected, an attack on a third party in the chain can have devastating consequences.
Why are we at HANSE Interim addressing this topic? Because defending against such risks is no longer just a technological task – it’s also an organizational and leadership challenge.
This is exactly where experienced interim managers come in. They step in to close leadership and expertise gaps, coordinate crisis responses, build resilience across systems, and ensure that companies remain operational in critical phases.
Cybersecurity is no longer just an IT matter. It’s a board-level issue of strategic relevance.
Point of Attack: The Weakest Link in the Chain
Unlike traditional hacker attacks, supply chain attacks target areas where protective measures are often weaker: external partners. Cybercriminals infiltrate software updates or manipulate hardware components, assuming they will be used in the target company without further checks.
This results in a stealthy intrusion that often remains undetected for weeks or even months. A prominent example is the SolarWinds hack in 2020, in which 18,000 companies and US government agencies were compromised, including the Department of the Treasury, the Department of Homeland Security, and major Fortune 500 corporations.
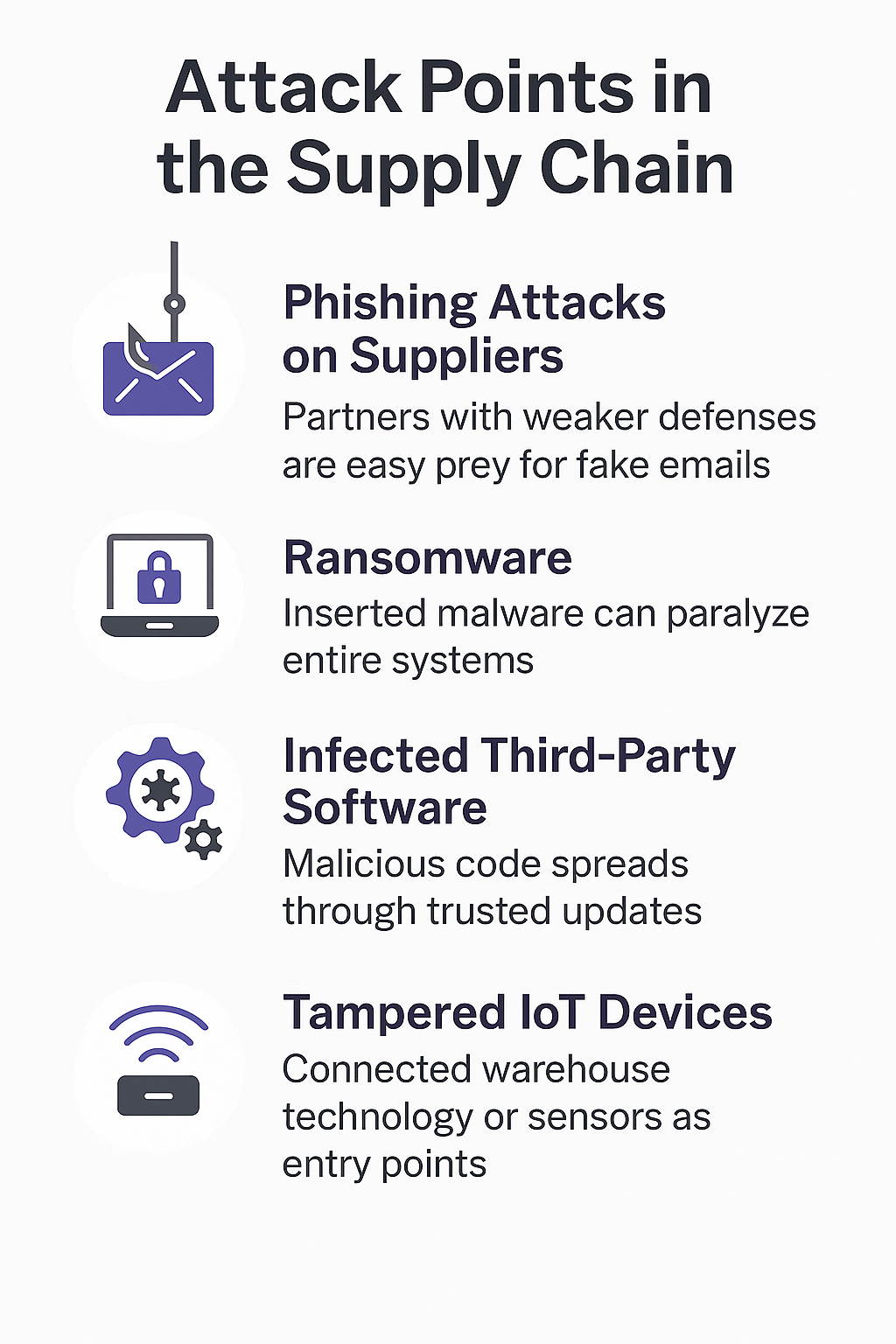
Four Common Entry Points in the Supply Chain
- Phishing at suppliers
Less protected partners are easy targets for fake emails and identity theft. Often, a single click on a malicious attachment is enough to steal login credentials. - Ransomware
Once inside, attackers can paralyze entire systems and demand ransom. It’s not just about encryption anymore – they also threaten to release sensitive data. - Infected third-party software
Malware is distributed via trusted software updates. This is especially critical for widely used tools that affect many companies at once. - Manipulated IoT devices
Connected warehouse technologies or sensors can serve as points of entry. As automation increases, so do new vulnerabilities – often poorly secured.
The Scope of the Threat
Between 2021 and 2023, supply chain attacks increased globally by 431 percent. In 2024, more than one third of all security incidents were linked to third parties, according to the Global Third Party Breach Report. In Germany alone, cyberattacks caused an estimated 180 billion euros in damage. Even more concerning: over 60 percent of German companies now see cyber risks as a threat to their very existence.
Hotspots are also emerging geographically. In 2024, North America accounted for 57 percent of reported cyberattacks, followed by Europe (24 percent) and the Asia-Pacific region (13 percent). Africa saw an average of 3,370 attacks per organization per week – a 90 percent increase year over year. Sources range from state-backed groups to highly organized cybercrime networks.
From Data Theft to Production Shutdowns
The consequences of an attack range from loss of trust and operational disruptions to legal repercussions. For example, the NotPetya attack in 2017 spread via a compromised update and brought companies like Maersk, Merck, and FedEx to a standstill. The global damage was estimated at over 10 billion US dollars.
In addition to production downtime, sensitive data such as blueprints, customer data, or intellectual property may be stolen. This can severely impact a company’s competitiveness and market position. Under the General Data Protection Regulation (GDPR), substantial fines may also apply.
Resilience Instead of Risk: What Companies Must Do Now
Cybersecurity in the supply chain requires clear strategies and consistent execution:
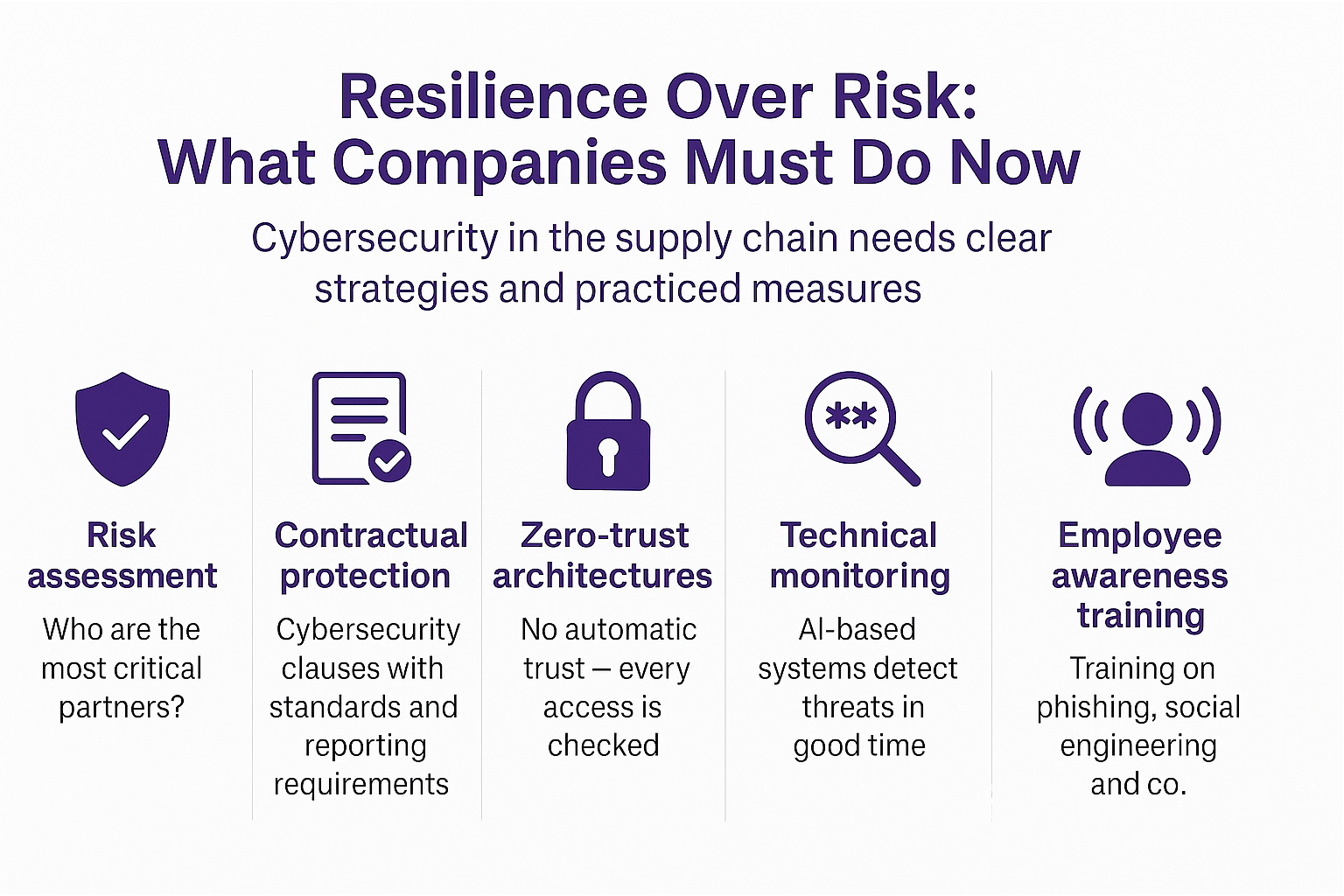
- Risk assessment
Which partners are most critical? Which systems are particularly sensitive? Where are the most vulnerable interfaces? - Contractual safeguards
Cybersecurity clauses with binding standards and notification obligations. It’s not just about paperwork, but about lived partnerships with clearly defined expectations. - Zero trust architectures
No automatic trust. Every access must be verified. This paradigm shift requires both technical and organizational changes. - Technical monitoring
AI-supported systems detect threats early. They learn from each interaction and often respond faster than humans. - Employee awareness
Training on phishing, social engineering, and more. Only informed teams can recognize and defuse attacks in time.
These measures should be supplemented by regular audits, emergency drills, and a documented incident response plan. Being prepared when it matters saves valuable time – and nerves.
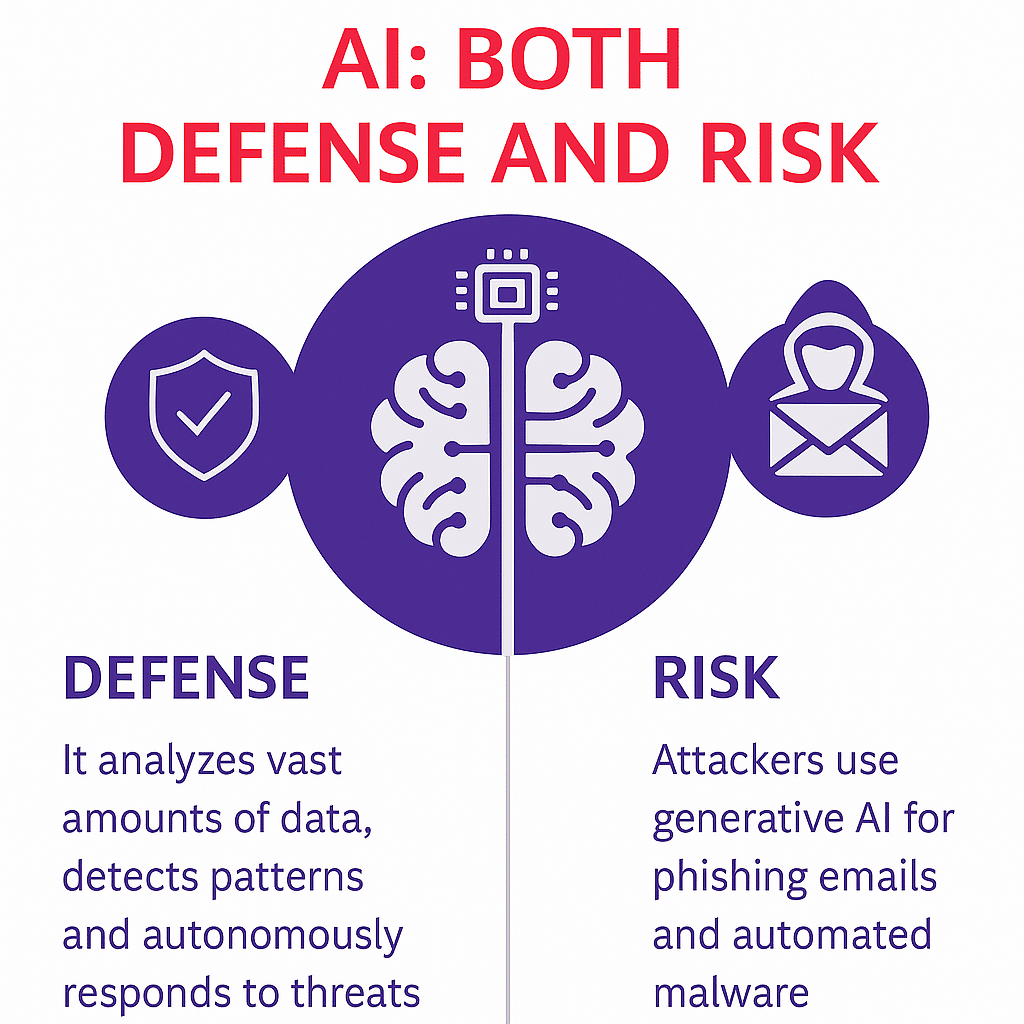
AI: Shield and Threat at the Same Time
Artificial intelligence plays a double role in cybersecurity:
- As a defense
AI analyzes vast amounts of data, identifies patterns, and reacts autonomously to threats. It is particularly effective in automated vulnerability detection, code review, and real-time monitoring. - As a risk
At the same time, attackers use generative AI to create highly convincing phishing emails or automatically generated malware. The professionalization of attacks is advancing rapidly. According to Germany’s Federal Office for Information Security (BSI), large language models can already generate, modify, and adapt code specifically to bypass security systems.
On top of that, deepfakes, synthetic voices, and chatbots give social engineering attacks a new dimension. The line between real and fake is becoming increasingly blurred – even experienced IT teams face growing challenges.
Interim Management: When Speed Matters
Especially in exceptional situations, decisive action counts. Interim managers with experience in IT and crisis management offer not only technical expertise, but also leadership strength, independence, and implementation skills.
Their contribution includes:
- Immediate coordination of security measures in emergencies
- Building resilient structures for IT and supply chain security
- Stabilizing teams and internal communication
- Awareness programs and employee training
- Support in implementing zero trust frameworks and continuity plans
- Assistance in selecting and rolling out secure third-party solutions
Interim managers act as a bridge between IT and executive leadership. They translate technical risks into strategic decisions. When time, resources, or internal expertise are lacking, they make the difference.
Conclusion: Think Holistically, Act Decisively
Cyberattacks on supply chains are not isolated incidents – they reflect a new risk reality. Companies need more than just technology. They need a culture of security, supported by clear processes, transparent leadership, and experienced execution.
Interim managers play a central role in this. They act quickly, effectively, and with a sense of responsibility. Those who invest today are not just protecting data – they are securing their future viability in an increasingly digital and interconnected world.
Best regards
Your HANSE Interim Management
Andreas Lau


